
In MITM attack framework perpetrator can take position between a a user and an application conversation and try to access information. The main purpose of this attack is to steal personal information like login credentials, personal data etc. A man-in-the-middle attack allows an attacker to intercept data, send and receive data meant for someone else.
Xerosploit is a tool which is used to perform MITM attack. This is a python based framework which combines the power of bettercap and nmap. This tool has driftnet modules which capture images and it also can be used in performing injection attacks.
(Hardware requirements- WIFI compatible with kali Linux which support packet injection and monitor mod.) Click here to get one for yourself.
As Xerosploit is not preinstalled in Kali Linux, so follow these following steps to install Xerosploit-
Step1- Installation
Type- git clone https://github.com/Lionsec/xerosploit This will start cloning.
When cloning is done then type- cd Xerosploit/
You will see a file name install.py
Now to run that file (install.py) simply type- ./install.py
If you use Kali Linux then select number 1 and if you use parrot os then select number 2. This will start installation.
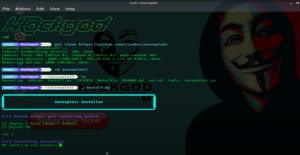
But after installing you will see two errors. The cause of these two errors are tabulate and terminaltables.
Step2- Fix Error
So now you have to solve those two errors. First, copy the name (tabulate) then type- pip install and paste the name. Do same for the second one.
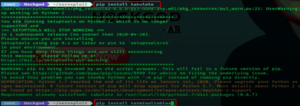
After this is done again run the file (./install.py) and this time the Xerosploit will be installed without no error.
After installing it must update your system and now it’s ready to use.
Step5- Run and attack
Now open a terminal and type Xerosploit This will just start running the script.
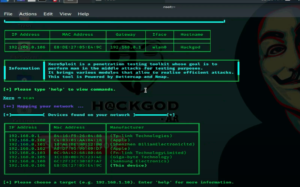
Then type scan to scan the connected wifi network. After the scanning completed you will be able to see the all connected devices with the same network including IP address and Mac address.
Now first copy and paste targeted device’s IP address.
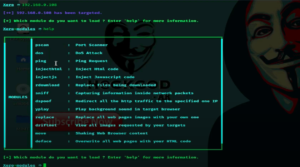
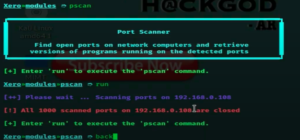
- For port scanning type
pscanand run it. If you see all the ports are closed then again typebackand try another module.
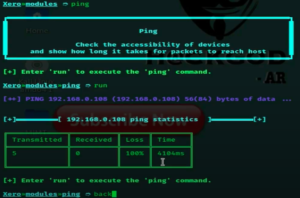
- To get ping requests type
pingand enterrunand then again go back.
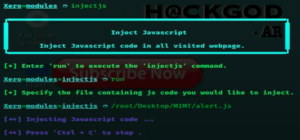
- Now if you want to inject JavaScript code type-
injectjsandrun. Then just copy and paste the path of java script you want to inject. Now click enter and it will start attack. When the attack is done typebackand try another.
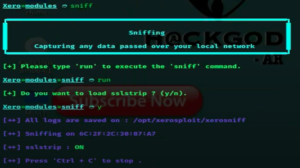
- Now let’s try sniff attack. Type-
sniffandrun. It will ask if you want to load SSLSTRIP, so enter y and it will start attack to your targeted device. In this attack you can access all the information from targeted device. Press “ctrl+c” to stop the attack.
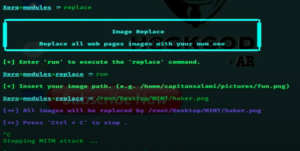
- Let’s try image replace. Type-
replaceandrun.Now copy and paste the path of the image and click enter to start the attack. This will start panic attack. To stop the attack press “ctrl+c”.
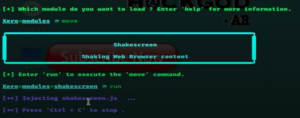
- You can shake the web browser content of your target device. To try this panic attack type-
moveand thenrun. To stop this attack press “ctrl+c”.
So, as you can see Xerosploit is quite interesting and useful as well for performing so many attacks. You can also try other commands and see those interesting commands perform on your target device. However this method is a basic method. So this will only will work on websites those have no SSL certificate.
What’s your reaction?
Leave a Reply
You must be logged in to post a comment.








Leave a Reply